"Implementing LDAP on Linux isn’t exactly difficult once you know the right changes to make. For reasons I cannot explain, however, most information I have read about LDAP seems to convey just how much trouble the author had implementing it. Finding the right changes in the first place is usually the most challenging part. Linux distributions could automate this process a little more; having front ends to server and client configuration would take Linux far in the LDAP world."-- https://www.linux.com/news/linux-ldap-authentication/ 2005
"
ROFL:ROFL:ROFL:ROFL
___^___ _
L __/ [] \
LOL===__ \
L \___ ___ ___]
I I
----------/
"
-- Me (2019)
Do:
sudo apt install ldap-utils libpam-ldapd libnss-ldapd nscd libpam-mklocaluser
/etc/nsswitch.conf (I think I had to put "ldap" on the three lines.)
# /etc/nsswitch.conf # # Example configuration of GNU Name Service Switch functionality. # If you have the `glibc-doc-reference' and `info' packages installed, try: # `info libc "Name Service Switch"' for information about this file. passwd: ldap compat systemd group: ldap compat systemd shadow: ldap compat gshadow: files hosts: files mdns4_minimal [NOTFOUND=return] dns myhostname networks: files protocols: db files services: db files ethers: db files rpc: db files netgroup: nis
/etc/ldap.conf(just the uncommented lines)
host diskstation.lan base dc=lan ldap_version 3 rootbinddn uid=admin,cn=users,dc=lan pam_password md5
/etc/pam.d/common-account /etc/pam.d/common-auth /etc/pam.d/common-password
finally
sudo /etc/init.d/nscd restart
Gotchas
Don't forget to restart nscd/nslcd services
Make sure the local user (the one used to setup the machine) and the ldap user's UID/GID match. Default Linux first setup user is UID=1000/GID=1000; default LDAP is UID=1000001/GID=1000001. When LDAP login takes over, the LDAP numbers start working, and permissions don't work anymore, since 1000=/=1000001. The names listed are correct in all ls -l commands, so it gets hard to track down. Use id instead. I changed my ldap UID/GUID to 1000, because I didn't want to change the local one with every new computer setup. I guess I could have a real admin account on the machines...
ldapsearch doesn't use /etc/ldap.conf, so it isn't helpful verifying the files.
Example LDAPSEARCH to see everything:
stephen@compy~$ ldapsearch -h diskstation.lan -x -b "dc=lan" # extended LDIF # # LDAPv3 # base <dc=lan> with scope subtree # filter: (objectclass=*) # requesting: ALL # ...
also jexplorer for gui-ness
tail /var/log/auth.log:
tail /var/log/auth.log:failed to bind to LDAP server ldapi:///diskstation.lan: Can't contact LDAP server"doesn't mean the url is wrong. Use "host diskstation.lan" not "uri ldapi:///diskstation.lan"
"
failed to bind to LDAP server ldap://diskstation.lan: Invalid credentials"Doesn't mean the password is wrong,
rootbinddn might be wrong. It needs a "uid" and a "cn" and a "dc"
/etc/ldap.conf
host diskstation.lan…rootbinddn uid=admin,cn=users,dc=lan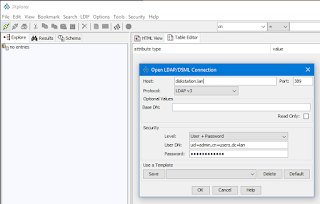
No comments:
Post a Comment